Why do you need Active Monitoring with Zero Trust?

Introduction
Since its introduction in 2009, Zero Trust has been adopted by major government organizations (DoD and CISA) and tech giants (Google, Microsoft, etc) alike. As of 2023, 68% organizations are planning or actively working towards adopting a zero trust access model.
By treating external and internal users both as potential malicious actors, requiring authentication at each step, and limiting lateral movement by restricting access to only what is required (least privilege), Zero Trust framework of cyber security has proven to be extremely effective at keeping malicious activity at bay.
Dataversity reported that the Cisco data breach of 2020 could have been prevented by a zero trust network access. The ex-employee whose credentials were exploited by the attackers, could have been removed from the system with a proper access management system; a characteristic of zero trust framework. Organizations employing Zero Trust realize 20.5% lower costs in data breaches than otherwise.
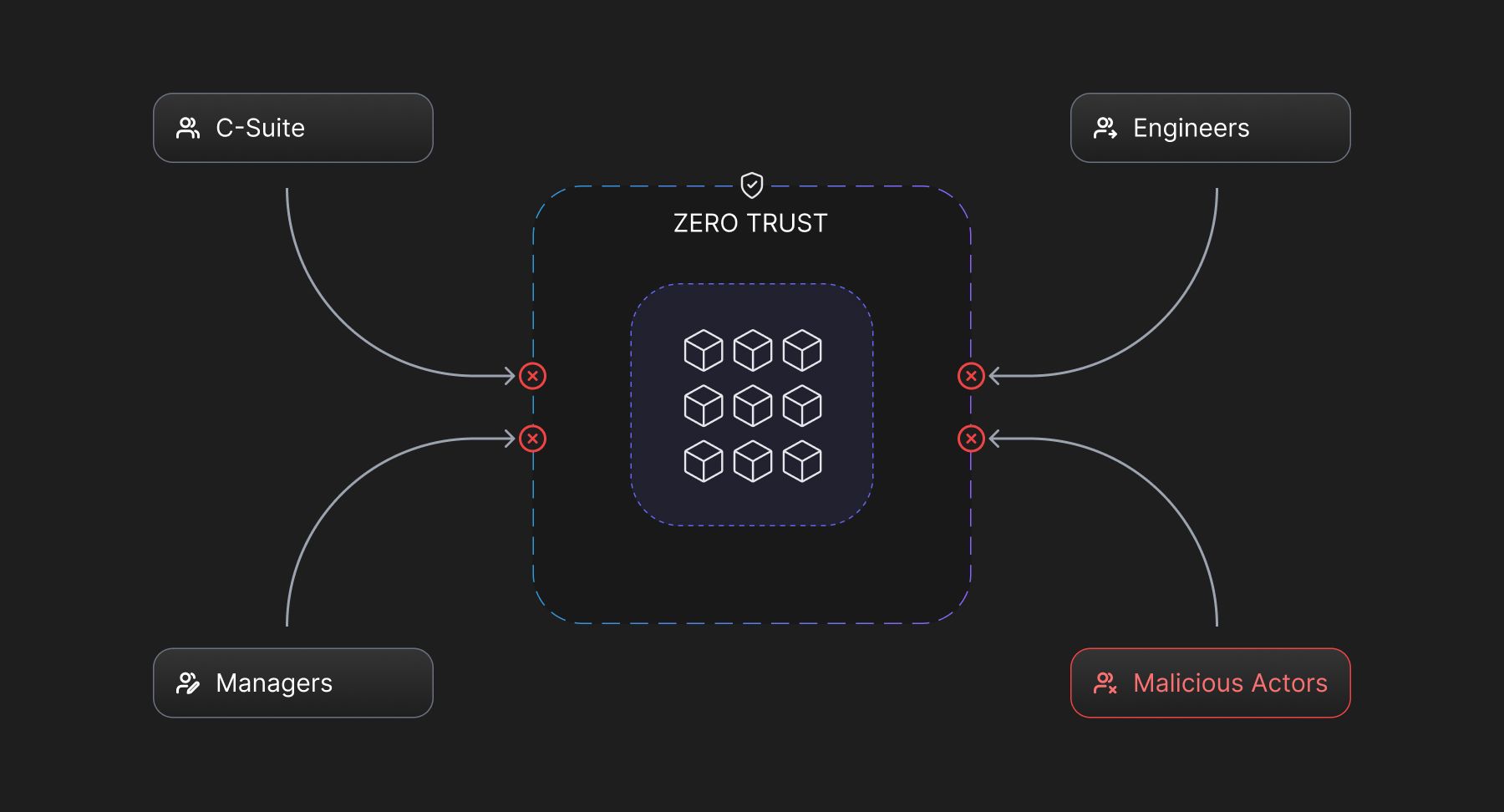
The Limitations of Zero Trust
Zero Trust is a challenging concept to understand, and even more difficult to implement and maintain. Different providers lead their implementations with different base definitions, leading to variations in how it is applied across different services.
Over-Privileged Accounts
The best chance for attackers to access a zero trust network is by exploiting its most privileged members. These accounts are those of the admins and people in managerial positions which are often not well monitored by design of the organization. While Zero Trust enables equal scrutiny of all the members, constant monitoring into all access activity is required to maintain a good Security Posture.
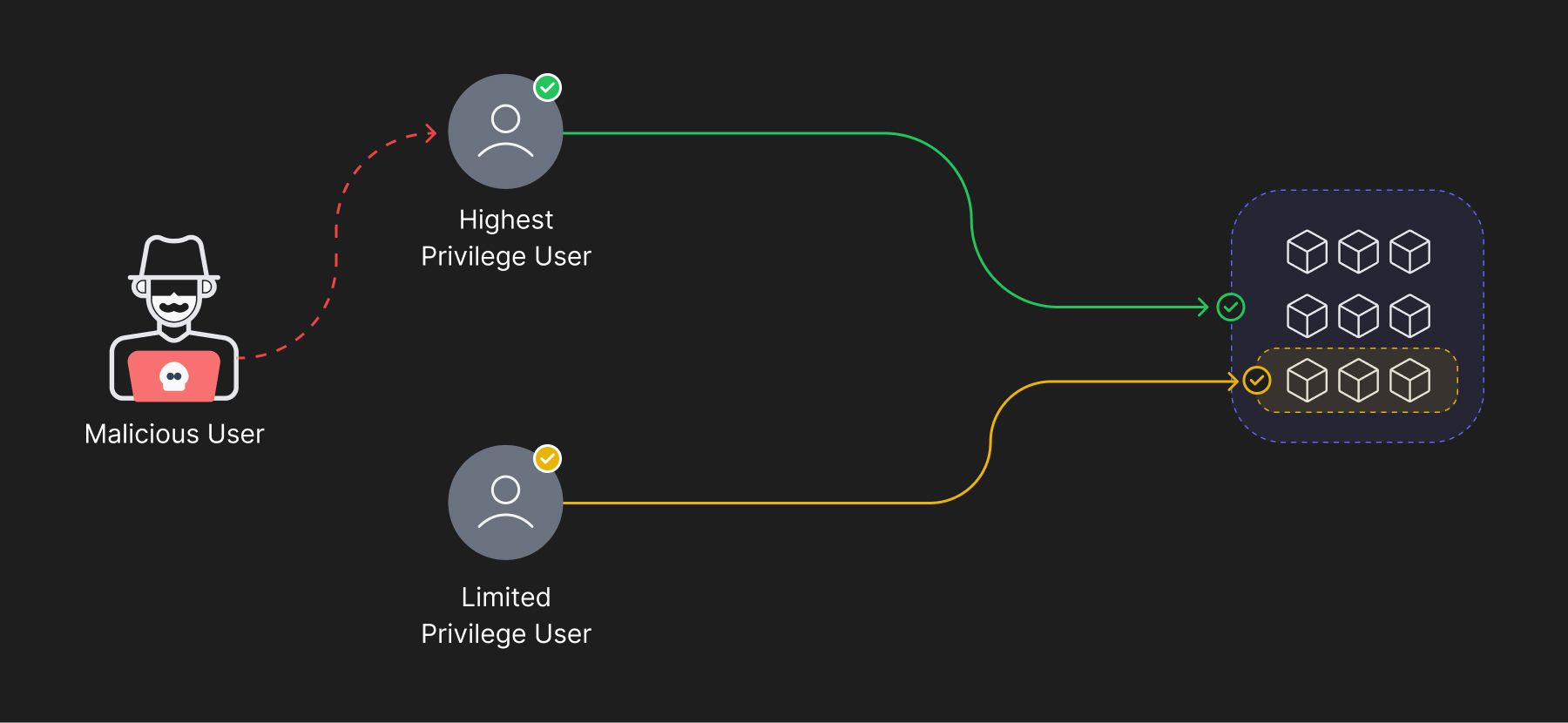
Containing Lateral Movement
While Zero Trust is designed to contain attackers and limit their movement within the network, detecting and preventing lateral movement can still be challenging, especially if the attacker has compromised other parts of the network.
An organization’s efforts can be targeted to controlling access to a certain database, while the attacker would be exfiltrating data from other resources. Such scenarios are possible where the attacker gained access to many credentials through an elaborate social phishing attack. An ongoing effort into monitoring every event and setting alerts on the first signs of malicious activity is therefore important for quicker remediation and containment of the attack.
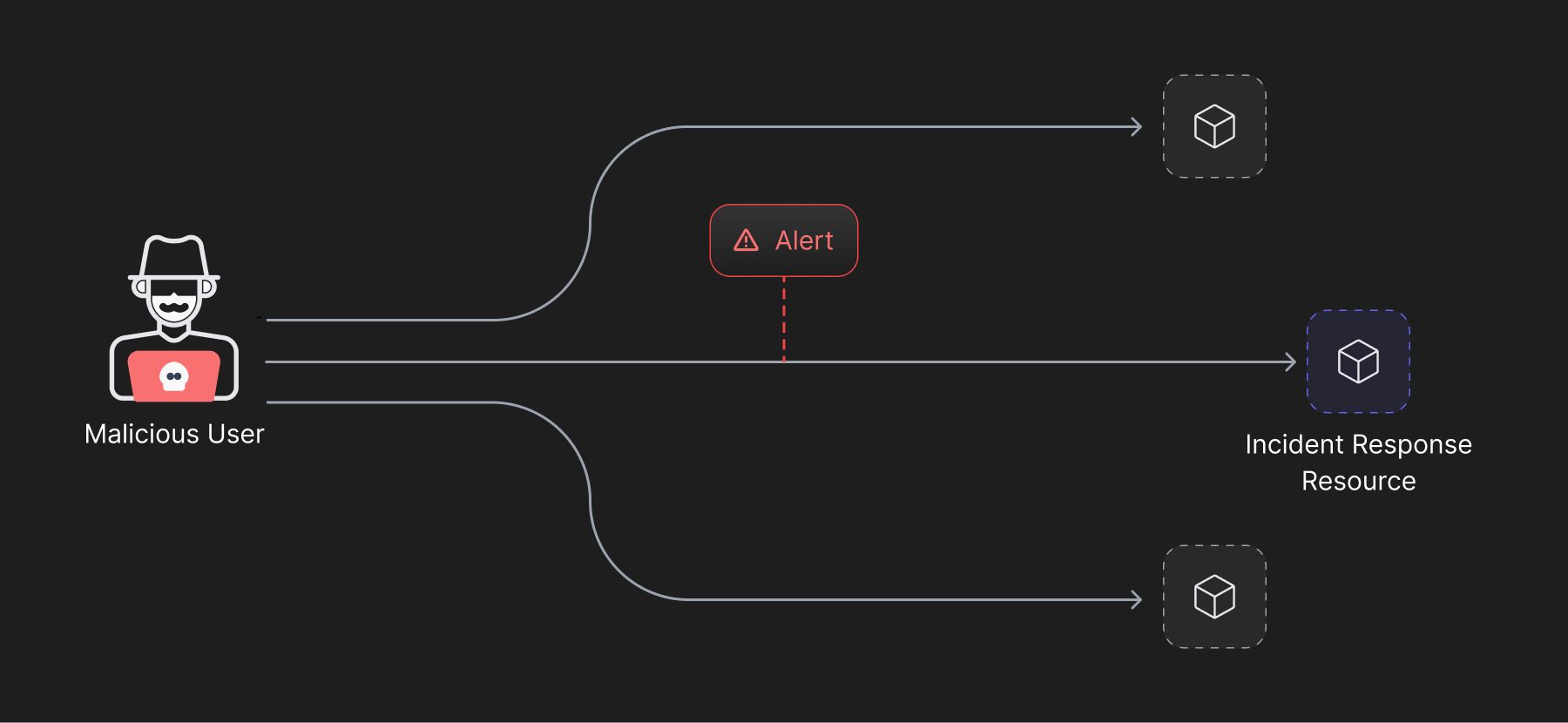
Controlling Device Access
Growing organizations need to increasingly control device access along with user permissions. Risk based management of device access can get overly complex when the security team has to focus on many considerations including inbuilt hardware security, IP address, type of network device is connected to, third-party app permissions, among others. This adds another layer of complexity to the already complex Zero Trust Implementation. Added considerations despite making the system more effective, also introduces faults, which are a characteristic of sophisticated architectures.
A simple way out proves to constantly monitor database activity, and run threat detection models that alert the monitoring teams of any potential malicious activity.
“Only” Zero Trust isn’t the ultimate weapon
Although both big tech and governmental organizations have embraced Zero Trust in their operations to enhance their security, they are still vulnerable to certain threat vectors. As security teams, we cannot wait for a breach to occur as proof of the system's vulnerability to an attack. Instead, we must analyze all potential avenues and ensure that the security posture effectively detects and prevents these threats in the future.
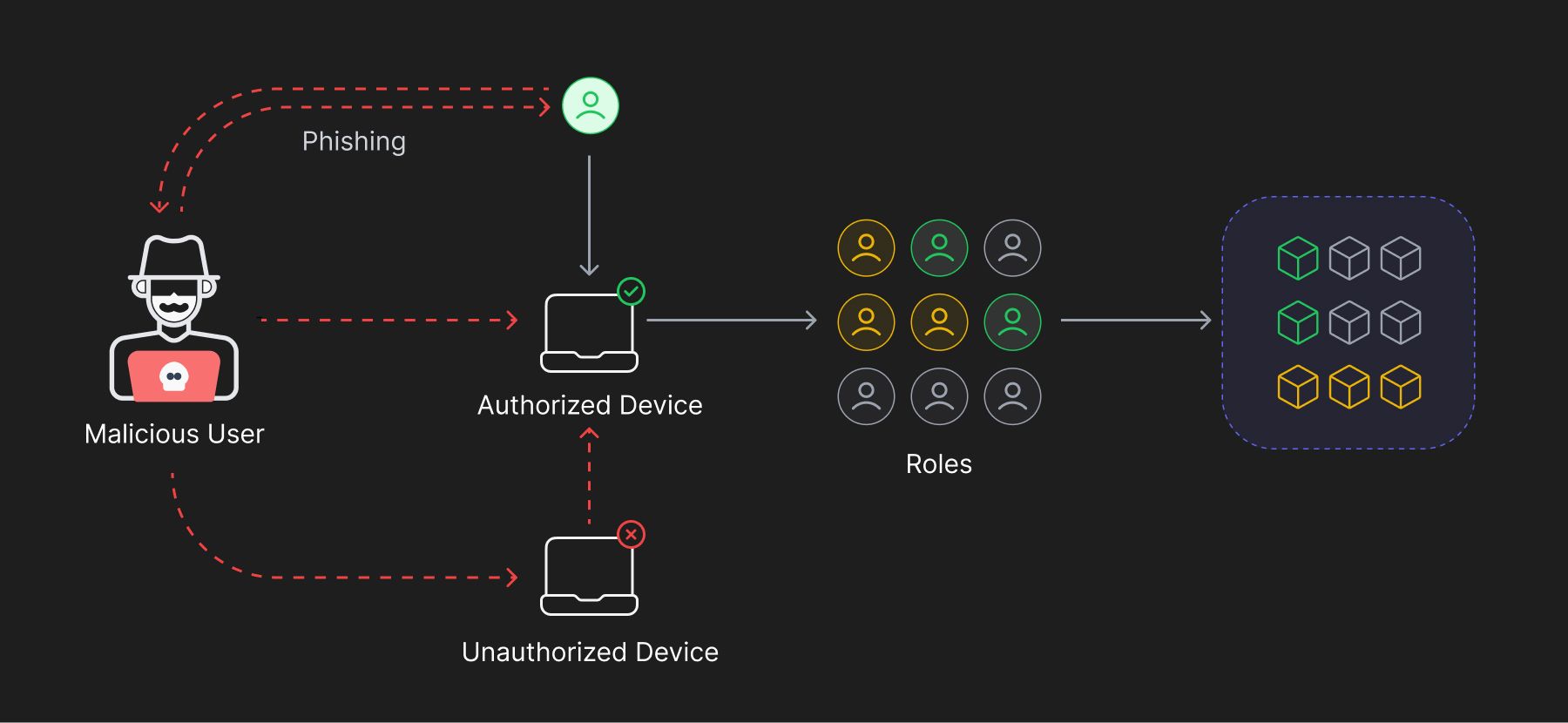
Credential Sprawl - With improper infrastructure access management (IAM) practices in place the organization is susceptible to credential sprawl, even when zero trust is implemented. Privileged users might access privileges through multiple disparate devices, leaving a bigger attack surface.
Vulnerable devices - Even after strong access management and Zero Trust in place, lack of visibility over fragmented identities, organizations can be vulnerable to internal and external threats. This means that if an organization does not have a clear understanding of who and what has access to their corporate assets, they may not be able to detect anomalous behavior.
Social Engineering Attacks - Even the smartest people fall prey to social phishing attacks aimed at stealing credentials from a user. Zero trust can insure only privileged users can access resources, however, it fails to effectively identify the actual user accessing their resources, even after implementing risk based authentication.
Need to Constantly Monitor Activity and Automate Violation Detection
Zero Trust is a strong framework and has been effectively implemented by many providers. Over the years Zero Trust has evolved to include many tools such as Granular Access Management, Risk Based Authentication, and most importantly; Database Activity Monitoring (DAM).
Activity Monitoring has been a focus of security teams for many years and has made significant progress. In the past, tool providers used network sniffing to monitor network bandwidth and identify users who were using excessive resources. While network sniffing worked great with interconnected networks operating locally, it fails for multi-cloud infrastructures that have a lot of isolated resources and a lot of access points.
Additionally, network sniffing is a passive tool, which collects all data which then has to be used by analysts to figure our any unusual activity. With new exfiltration methods, where the attackers transfer data slowly, over a period of time, network sniffers will completely fail to detect breaches until it is too late.
DAM is a set of practices to actively monitor any and all activities to monitor manipulation of an organizations data to detect threats and quickly remediate any breach impacts. It uses real-time network monitoring to detect any policy violations that were set in place by the security team.
Active Monitoring and Zero Trust with Adaptive
Adaptive provides a framework of tools and services to actively detect vulnerabilities by monitoring database activity in near-real time taking counter measures such as blocking access as soon as something doesn’t seem right.
It does this by implementing a Zero Trust network and creating short lived ephemeral bastion hosts which enable a robust access control for the organization’s admins while also enable active database active monitoring of each and every privileged individual to the organization’s resources.
 SOC2 Type II
SOC2 Type II

