What is the Principle of Least Privilege (POLP)?

What is the Principle of Least Privilege?
We live in an age of hyperconnectivity and ubiquitous computing, which has led to the emergence of advanced cyber threats. News reports of massive data breaches affecting businesses from fledgling startups to large corporations have become increasingly more common. Protecting sensitive information and making their security infrastructure more robust, has thus become one of the, if not THE primary concern of organizations all over the world.
In mitigating these risks that organizations are faced with on a constant basis, The Principle of Least Privilege plays a crucial role. The Principle of Least Privilege (PoLP) emphasizes limiting a user's access to only the minimum set of resources required to complete a task (least privilege). By following the Principle of Least Privilege, organizations can reduce the probability of unauthorized access, and minimize the blast radius in the event of a breach.
How does the Principle of Least Privilege Work?
PoLP works by limiting user access and permissions to only the absolute minimum required to perform their tasks. Here, the user can be a human user or any process or entity that requires access to the resources under question. Limiting access this way reduces risks like Privilege Creep, where users end up accumulating privileges over time, as they work on new tasks or move to new roles or departments, requiring new privileges, while older, unnecessary privileges may remain un-revoked. In following the Principle of Least Privilege, users are granted access to resources on a strictly need-to-know basis, which can prevent unauthorized access. Some well-known strategies for implementing PoLP include Just-in-Time PAM and Role-Based Access Control.
Just-in-Time Privileged Access Management (JIT PAM)
Where a user is temporarily granted privileges to resources that are essential to perform a task, for no longer than is necessary to perform a task. Thus, the privilege is restrictive in scope as well as in time. Privilege Bracketing works on this principle.
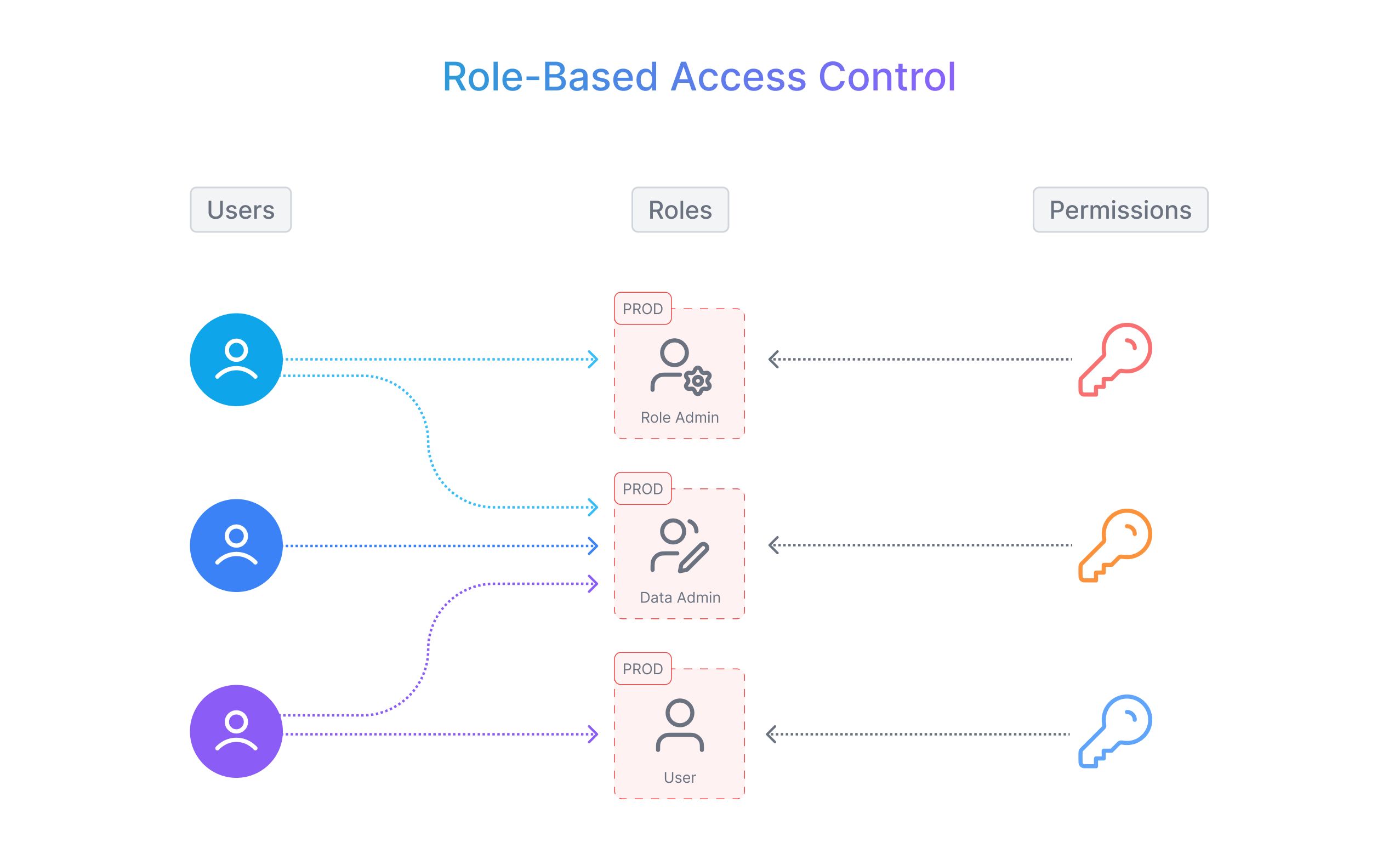
Role-Based Access Control (RBAC)
Where roles are assigned to users based on job function. Under this role, the user has access only to those resources defined by the role. As such, individual users are not directly assigned permissions, and inherit permissions from their roles.
For example: Under RBAC, an employee in the Payroll department of an organization who wants to prepare monthly summaries using a payroll table in the database will be assigned the payroll role, which may provide read-only access to only that table.
Principle of Least Privilege in Action
Examples of enforcing the Principle of Least Privilege can be found on many levels and across multiple subsystems of IT infrastructure. Some of the more widely known practical applications can include filesystem permissions on Linux or UNIX-like OSes, user privileges in Relational Database Management Systems such as MySQL, and more recently, Identity and Access Management (IAM) systems on cloud platforms like AWS and Google Cloud.
File and directory permissions in Linux
Linux file permissions allow for the implementation of the Least Privilege Principle by restricting user/process access to files and directories. Every file and directory has read, write, and execute permissions at owner, group, and other levels.
IAM in Amazon Web Services (AWS)
AWS Identity and Access Management (IAM) enables the implementation of the Principle of Least Privilege by providing control over user permissions to AWS resources such as EC2, S3, Lambda, and more. Within the IAM console, administrators can create fine-grained policies that specify the actions that a user or group can perform on AWS resources. Policies can be tuned to grant users and other AWS resources only the necessary permissions, minimizing the potential damage from security breaches or unauthorized access.
Databases
The Principle of Least Privilege can be implemented on popular RDBMS systems like MySQL, Postgres, Oracle, and Microsoft SQL Server using the GRANT statement, which can be used to define read, write, update, delete, drop, and alter access to tables for database users.
These RDBMS platforms also provide more fine-grained row-level security e.g. Postgres' Row-Level Security feature. Row-level access control can be implemented by using views, where only the necessary rows in a table that the user needs access to can be stored as a view, and providing read access to the user to these views, instead of the underlying table itself.
Among NoSQL databases, MongoDB provides an implementation of Least Privilege through RBAC described above. A database administrator can define roles, which can be applied at the level of an individual user, or groups of users.
Best Practices for Implementing the Principle of Least Privilege (PoLP)
 It is recommended to perform a thorough audit of your organization's existing security infrastructure before you get started with implementing the Principle of Least Privilege. This includes assessing existing users, resources, processes, and the security risks and mechanisms involved. After this initial assessment, we can follow these best practices:
It is recommended to perform a thorough audit of your organization's existing security infrastructure before you get started with implementing the Principle of Least Privilege. This includes assessing existing users, resources, processes, and the security risks and mechanisms involved. After this initial assessment, we can follow these best practices:
1. Define user roles and access levels
After identifying the different types of users who will access the system and the resources they access, define roles and access levels for each role and the privileges associated with those roles. This is Role-Based Access Control (RBAC) in action. Several standards for implementing RBAC exist including the National Institute of Standards and Technology's NIST RBAC system.
2. Limit access based on need
Minimize access to the bare minimum number of resources required by the user, an additional layer of security can be added by making the access time-bound.
3. Authentication and authorization controls
Robust authentication mechanisms, such as multi-factor authentication (MFA), should be employed, by which only authorized users can access resources.
4. Monitoring
Effective monitoring involves the use of various tools to identify potential security risks and prevent incidents. Intrusion detection and prevention systems, log management solutions, and firewalls are examples of such tools. These tools are essential for organizations in proactively monitoring their systems and infrastructure and preventing breaches.
5. Regular reviews and policy updates
Regularly review and update access policies and user roles as users, systems, and processes in the organization change. Ensuring that privileges remain appropriate and up-to-date can help prevent security issues like Privilege Creep from arising over time.
The goal of every CISO (Chief Information Security Officer) should always be to Minimize Access to Maximize Security.
Benefits of Implementing the Principle of Least Privilege
1. Risk Reduction
Implementing the Principle of Least Privilege minimizes the risk of unauthorized access or misuse of resources that are critical to an organization. Well-defined, tightly controlled access policies can minimize the attack radius in the event of a security breach.
2. Easier Compliance Practices
Adhering to PoLP enables organizations to meet regulatory compliance requirements by ensuring that access to sensitive information is strictly controlled and monitored.
3. Improves System Performance
As an added advantage, limiting access can improve system performance by reducing the number of users and processes accessing critical systems and data.
4. Simplifies Access Management
If implemented well, the Principle of Least Privilege enables organizations to simplify access management by reducing the number of roles and permissions required.
5. Saves Costs
Implementing PoLP invariably results in an organization avoiding financial, and reputational costs as they minimize the risk of security breaches and the fallout occurring from them.
Relation to Zero-Trust Architecture (ZTA)
Zero-Trust Architecture or the Zero-Trust Security Model assumes that all access to an organization's resources must be subject to continuous verification and authentication, and no user or entity trying to access these resources should be automatically trusted. In short, "Never Trust. Always Verify".
The Principle of Least Privilege draws parallels to ZTA with regard to minimizing access using Role-Based Access Control and Just-In-Time Access Management implementation.
 SOC2 Type II
SOC2 Type II

