Is your network safe from the One Click Attack?

Technocrats like to laugh and sneer at the sight of an actor typing away at a computer and suddenly breaking into a highly secured network to stop a nuclear attack, steal data, or perform some crazy deed to either save humanity or destroy it. While on television, the actor seems to finish the hacking in minutes, and on-demand, the reality is very different. However, with advancements in AI, it might be shifting quickly.
A recent study performed to test LLMs’ capabilities in identifying and exploiting vulnerabilities in a network shows that the state-of-the-art models, like GPT4 and GPT3.5, can do exactly that. With a success rate as high as 73%, these models can autonomously identify vulnerabilities in a network and successfully perform an attack.
The Study
“LLM Agents can Autonomously Hack Websites” is a recent study on the capabilities of constantly improving large language models. The authors of the study demonstrate how these models can successfully scout for vulnerabilities in a given system, and some can even successfully perform an attack by exploiting these vulnerabilities.
They also demonstrate that bigger models (bigger by number of parameters) follow the scaling law, i.e. the bigger the model the more capable it gets. The findings display the increasing effectiveness of bigger models in successfully exploiting the vulnerabilities as well as capable of performing more complicated attacks. Before exploring further, it’s imperative to understanding how attacks are manually performed.
Traditional way to attack a network
Traditionally, an attacker has to spend a lot of effort before initiating an attack. It involves deliberate planning and careful execution. The Cyber Kill Chain describes the 7 stages of an attack. The first three stages can be summarized as follows—
- Reconnaissance: This initial phase involves gathering information about the target. Attackers identify vulnerable targets and explore the best ways to exploit them. This could involve collecting publicly available information or using more covert methods to understand the target's systems and potential weaknesses.
- Scanning: Once a target is identified, attackers attempt to find a weak point that allows access. This often involves a slow and methodical search for vulnerabilities in the target's systems, such as misconfigurations, unpatched software, or weak passwords.
- Access and Escalation: After identifying a vulnerability, the next step is to exploit it to gain access to the system. Attackers then escalate their privileges to move freely within the environment, often targeting privileged accounts for their ability to act as insiders. This stage is crucial for establishing a foothold within the target's network.
After these three steps, the attacker can then perform any desired malicious activity in the accessed network. Nevertheless, for the attacker, this process is excruciatingly slow, as the process of identifying the vulnerability can take anywhere between a month to an year.
AI & Shifting paradigms
Over the last two decades, cyber crimes have been constantly on the rise and have been increasing exponentially. As better security measures are developed, attackers find innovative methods to exploit the system’s vulnerabilities. This has also led to substantial investments in cybersecurity both in the venture capital world, as well as at the organization level. Regulatory Audits have become more streamlined with companies like Drata and Vanta growing very fast. The world is waking up and implementing more stringent measures to protect sensitive information with India’s DPDP and Europe’s AI Act acting as recent examples.
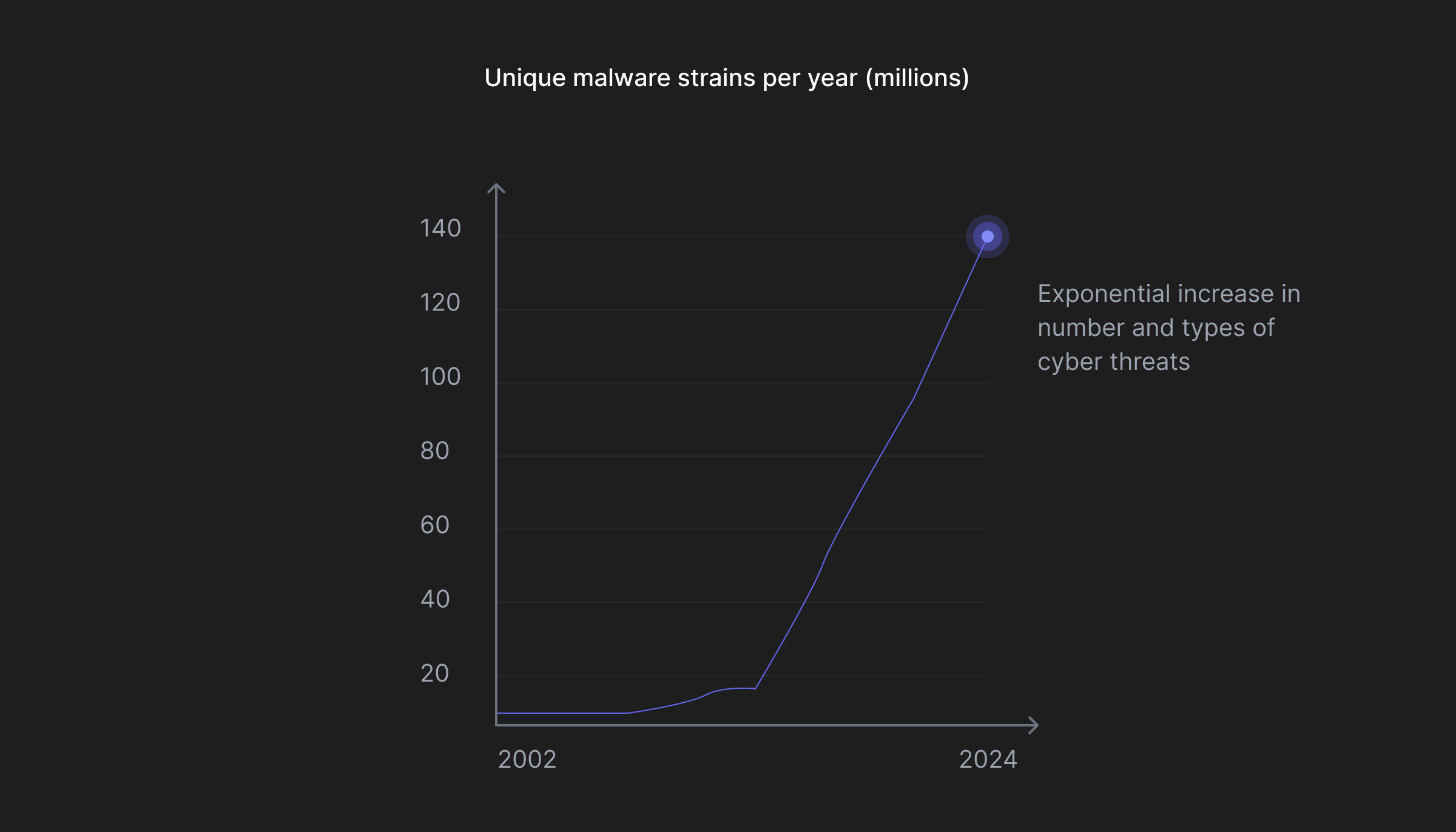
With new breakthroughs in AI happening almost every day, cyber attacks are bound to become more sophisticated as attackers find newer ways to exploit a system. The range of exploitative innovation that AI can enable ranges anywhere from phishing emails to duplicating your siblings voice for ransom. Today it is evident that one of the enabling factor for this acceleration is the wide development and adoption of AI across all domains.
Furthermore, with these advancements, what follows is an ever increasing pace of sensitive data generation. Information is being processed and generated at an all time high as more of the world goes digital. This makes more organizations prone to attacks, leaving the end consumer incapable of doing much when their data is compromised.
With all this advancement, Cyber attacks will only become stronger, and complex. And while today it takes a highly skilled hacker to perform them, tomorrow it can take a curious teenager to bring down a system.
The One Click Attack
The One Click Attack is a new AI enabled attack, that can autonomously start vulnerability detection and exploitation with just one click of a button. The study describes a reality where a well defined orchestration using very large (by number of parameters) Language Models (e.g. GPT4) are capable of identifying and successfully performing a cyber attack. The study also demonstrated that smaller open-source models (e.g. OpenChat 3.5) are good at quickly identifying vulnerabilities while not so much at performing an attack.
With just network identifiers, such as IP address or a domain name as input, the authors demonstrate the ability of this orchestration to identify vulnerabilities in the underlying network and perform a fully fledged attack. Their attacks were successfully able to compromise the system as much as 73% of the times.
The One Click Attack can then be described as initiating a well designed LLM agent (capability of function calling enabling it to perform actions) capable of compromising a well intentioned system within minutes (with just one click of a button required to start the autonomous operation) while learning from it’s prior actions. Such One Click Attack systems are capable of performing complex vulnerability discovery tasks by navigating systems, performing queries, and learning from the feedback received. They can even initiate a phishing attack by drafting and emailing privileged members of the organization.
What to expect in near future
While the study limits the attack types to 15 attacks and sandboxes it to 50 websites, it sheds some insights into the future. The findings describe such attack systems to follow the scaling law, i.e. they improve as LLMs become bigger and more capable. Over the duration of just 1.5 years, the world has seen drastic improvements in LLMs. It is improbable that this growth will slow down anytime soon.
More complex attacks (out of scope of the study), will become possible with constantly improving models. The exponentially increasing cyberattacks will also become more complicated as AI can identify vulnerabilities that are hard to identify, and exploit systems in previously unknown ways.
How to protect your organization?
Data is the ultimate asset for any organization making it the most crucial target for an attacker. For effective protection, organizations need to adopt a comprehensive data security stack. Real-time monitoring and anomaly detection on critical datasources is one of the more robust ways to detect and prevent data exfiltration.
On average, 1250 attacks are performed on each organization weekly. With One Click Attacks, this number will go higher and higher. Constantly improving Data security posture management, in turn, will increasingly strengthen the security.
Much like Target’s 2013 breach enabled by a third-party HVAC vendor having privileged access to their infrastructure, access escalation in case of an attack needs to be checked off. Managing access, in complement to activity monitoring can help quickly identify the source of attack and effectively contain it.
With managed security posture, access governance and activity monitoring, identifying and containing attacks can increasingly become more streamlined, decreasing the time to action. With these tools being able to interact with each other, automated threat models can effectively capture patterns and recognize threats as they happen, letting security teams to create automations for increased resilience.
 SOC2 Type II
SOC2 Type II

