Bits and Breaches - Target Data Breach 2013

Welcome to 'Bits and Breaches,' a new series by Adaptive exploring significant tech hacks. We'll unpack their effects and delve into preventative measures that could have averted them.
Why rehash the past, you ask? Because these aren't just old stories—they are pivotal lessons from history that continue to haunt the present.
The first story in the series is about Target, one of America’s favorite places to buy just about anything, and how a refrigeration and HVAC vendor cost them over $200 million.
Background of the 2013 Target breach
It was a cold day in December 2013, and the holiday season was in full swing. While merriment and cheer were everywhere, the day also bore witness to one of the largest data breaches in retail history. The breach occurred at the retail giant Target, affecting an estimated 110 million customers. Hackers made off with sensitive information such as names, addresses, email IDs, and telephone numbers, as well as 40 million credit and debit card records.
At the heart of the Target data breach lies a twisted tale of compromised credentials, bad network access setup, and the unlikeliest of accomplices: a third-party HVAC vendor named Fazio Mechanical Services. Yes, you read that right. It seems the cybercriminals behind the breach decided to turn up the heat, quite literally, by going after an HVAC company that had access to Target's network.
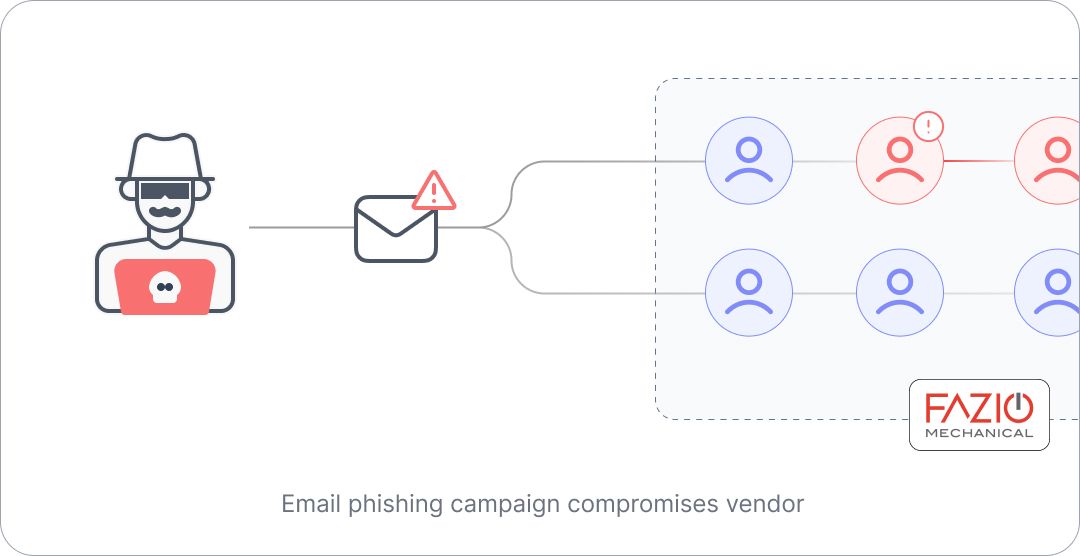
Here's how it went down: the hackers launched a spear-phishing campaign, sending deceptive emails to Fazio Mechanical employees. These emails contained malware that, once opened, harvested the employees' login credentials for Target's Vendor Portal. And just like that, the hackers had the keys to Target's digital kingdom.
But what does an HVAC vendor have to do with Target's payment systems, you ask? The retail giant's Vendor Portal was in the same network as the rest of the resources with sensitive information. So, the access to Third-party vendor portal allowed the hackers to move laterally within the network until they reached their ultimate goal: Target's Point-of-Sale (POS) system. Surprisingly, Target’s POS system was not isolated from the third-party Vendor Portal.
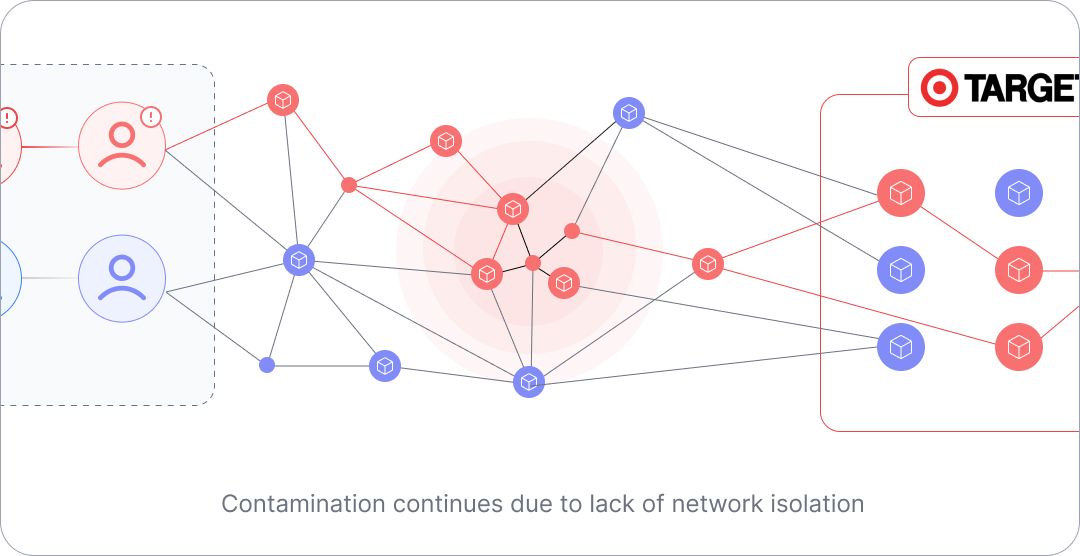
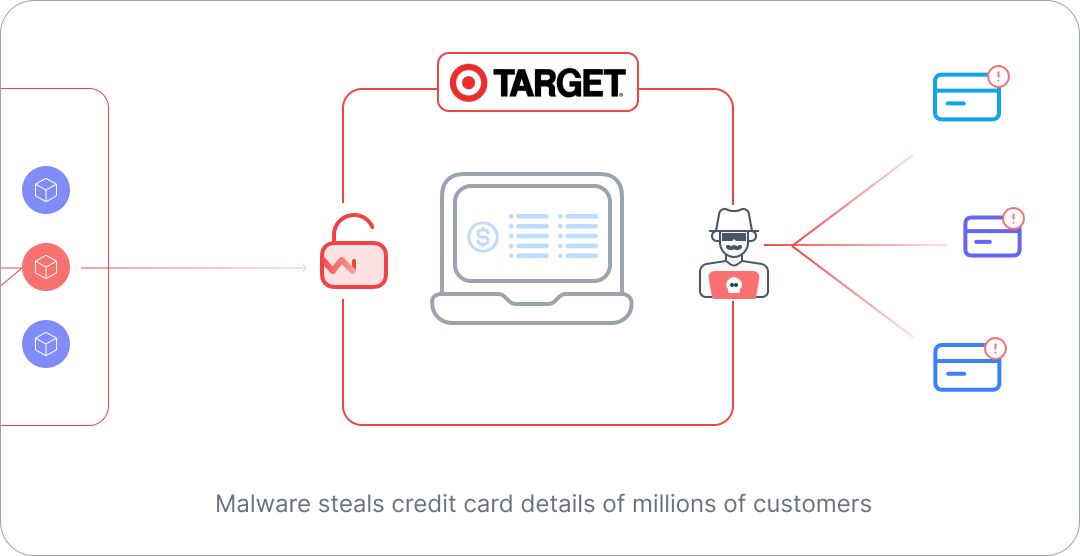
The attackers then installed custom malware on Target's POS systems, which captured and transmitted the credit and debit card data of millions of customers. This crafty heist went undetected for weeks, allowing the criminals to continue siphoning off sensitive information until the breach was finally discovered.
The Aftermath: Understanding the financial implications
The financial repercussions of the breach were staggering. Target incurred an estimated $162 million in expenses related to the breach, including costs for investigation, remediation, customer compensation, and legal fees. On top of that, Target settled with banks and credit unions for $39.4 million and agreed to a $10 million payout to customers affected by the breach.
In response to the breach, Target took several steps to improve its cybersecurity posture. The company hired Brad Maiorino as the new Chief Information Security Officer (CISO) to oversee its security and compliance efforts. Target also invested $100 million to upgrade its payment terminals.
Takeaway: How could this have been prevented?
The Target breach provided some much-needed lessons in the world of cybersecurity, serving as a wake-up call for organizations of all sizes.
A more effective strategy could have involved isolating various networks, especially the vendor portal. Network segregation, also known as network segmentation, is a security measure that separates a network into several subnetworks or segments. Each segment functions independently of the others, which means that if one segment is compromised, the others remain secure.
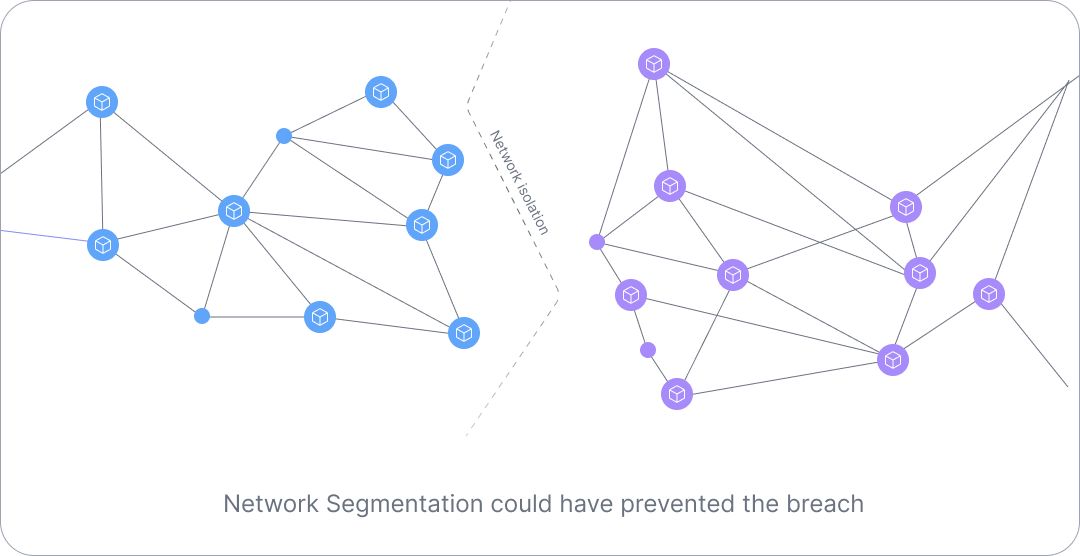
Many organizations, like Target, often believe that maintaining resources on a private network suffices for a secure stance. However, the truth is that relying on a singular private network presents considerable vulnerability. If this network is compromised, it becomes straightforward to scan and access all its resources. The major reason the breach incurred such a substantial financial toll was the lack of separation between the external vendor platform and Target’s other sensitive resources, including the POS system. These components resided within the same network, devoid of isolation. If Target had enacted network segmentation, it would have ensured that a breach in one part of the system wouldn't provide access to the billing platform, the repository of the most sensitive data.
 SOC2 Type II
SOC2 Type II

