Bits and Breaches - Sony Pictures

As we press play on our second article of 'Bits and Breaches’, we venture into the entertainment sector. Our focus today is Sony Pictures Entertainment, a household name synonymous with blockbuster movies and high-quality TV programming. In 2014, Sony Pictures experienced a major cyberattack, making it one of the most significant digital breaches a company had faced. But that’s not all!
In an unexpected twist, it came to light that the North Korean government was linked to this massive digital intrusion, a testament to the increasing complexity of international cybersecurity issues.
Background of the 2014 Sony Pictures Hack
As November 2014 dawned, the employees of Sony Pictures arrived at work, expecting another routine day. However, their screens were soon hijacked by a menacing red skeleton accompanied by the #GOP (Guardians of Peace) hashtag. The digital pirates had hoisted their flag, and Sony Pictures was under siege.

Unlike the hackers in our previous stories who discreetly siphoned off data, the Sony Pictures' attackers were loud and brash. They effectively crippled Sony Pictures' entire IT infrastructure, erasing data and rendering thousands of computers inoperable. But their destruction didn't end there. The attackers also stole vast amounts of data, including unreleased films, confidential emails, and personal employee data.
The notorious group claimed to have stolen 100 terabytes of data from Sony’s infrastructure and threatened to leak the most confidential data from it over the internet. This included Personally Identifiable Information (PII) of about 47,000 current and past Sony employees such as their addresses, driving license numbers, social security numbers, company credit card information, official travel details, etc. Also, they had access to confidential email communications between top Sony execs that talked about the actors, fees paid to them, corporate politics, and employee performance, and also revealed the salaries of the top brass at Sony.
GOP also got hold of 5 unreleased or recently released Sony movies in this data. They later leaked the movies through file-sharing networks over the internet including Brad Pitt’s movie Fury which supposedly was downloaded more than 1 million times from leaked sources during its first week in the theatres. The confidential email conversations as well were sent to journalists and reporters and eventually leaked to the public.
The initial incursion into Sony's systems was likely orchestrated through a tactic known as spear-phishing, a form of phishing that's more personalized and targeted. The hackers meticulously crafted misleading emails that appeared to be from trusted sources. These emails were then sent to a select group of Sony employees, with the aim of duping them into revealing their login information.
It is important to note that the effectiveness of spear-phishing relies on the human factor. In this case, Sony employees trusted and opened the phishing email. This type of social engineering relies heavily on psychological manipulation, encouraging hasty action or exploiting trust and familiarity.
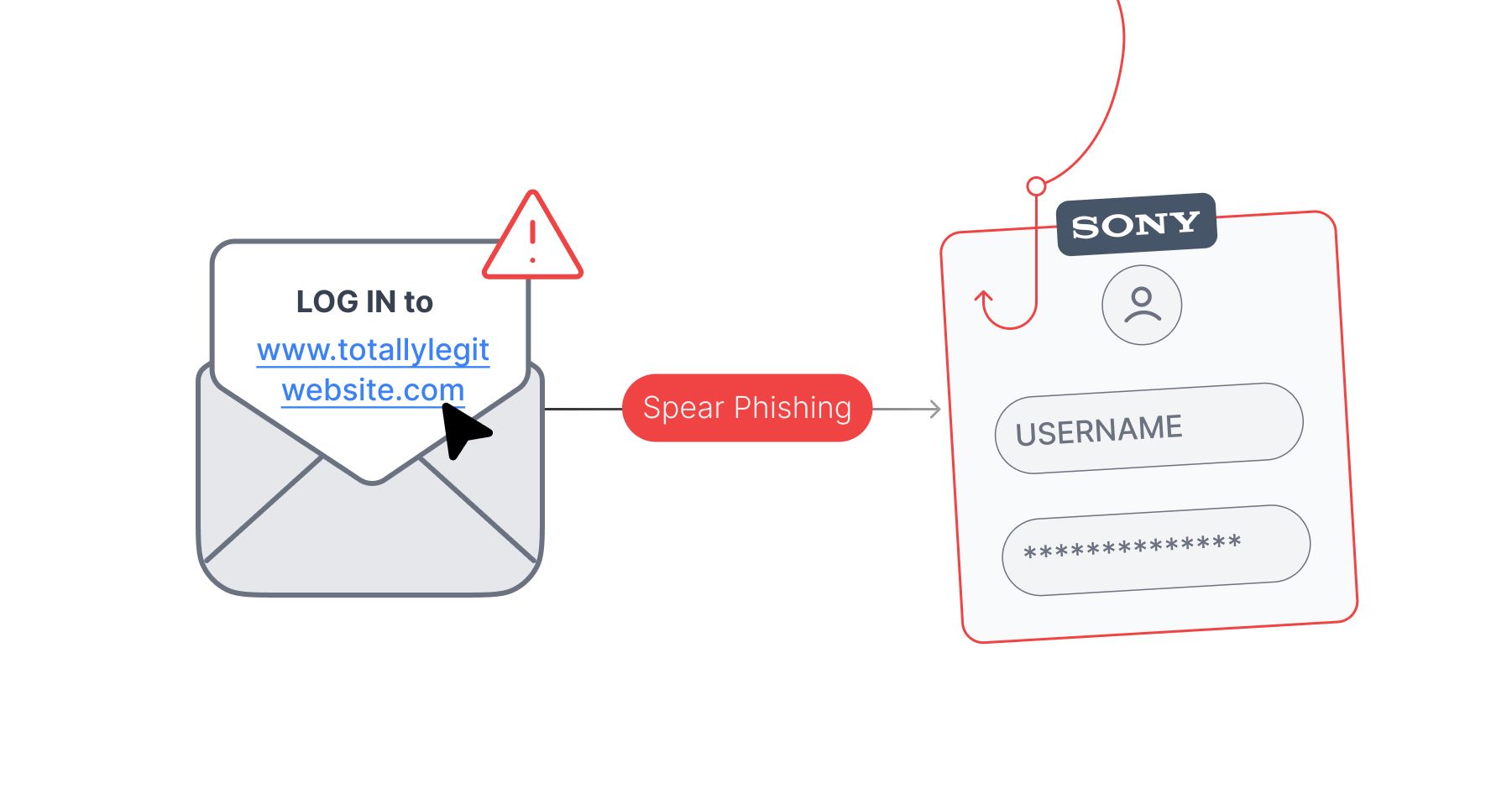
Once the attackers secured these login credentials, they essentially had the keys to the front door of Sony's network. However, penetrating a network's outer defenses is just the beginning. The next step is typically to escalate privileges within the system.
Privilege escalation is a process that takes advantage of system vulnerabilities, bugs, or configuration oversights to gain elevated access to resources that are usually restricted to regular users. In Sony's case, the hackers likely used a combination of known vulnerabilities and newly discovered "zero-day" vulnerabilities to accomplish this.
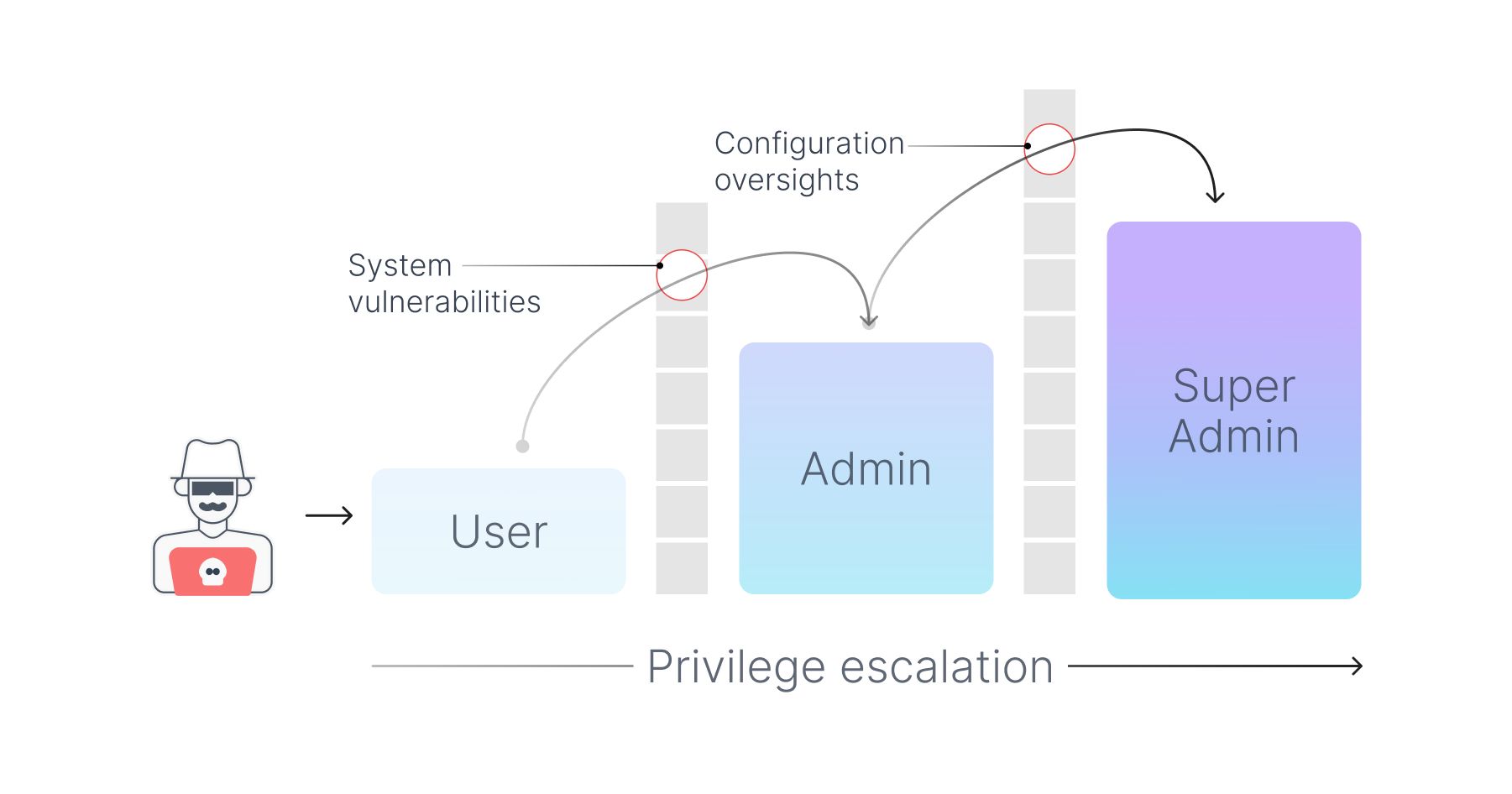
Having gained a higher level of system access, the attackers were then free to roam within Sony's digital estate, virtually undetected. They could take their time to carefully map out the network architecture, identify where valuable data was stored, and plan how to exfiltrate it.
When the time was right, the hackers initiated the extraction of Sony's data. This likely involved staging the data—collecting and organizing it in one place before sending it over the internet to a server under their control. Given the massive amount of data stolen, this process might have taken some time.
Finally, the attackers unleashed a wiper malware— a type of malicious software designed to erase data from the server or disrupt its operations. This not only caused further damage but also helped to cover their tracks, making forensic investigation more challenging.
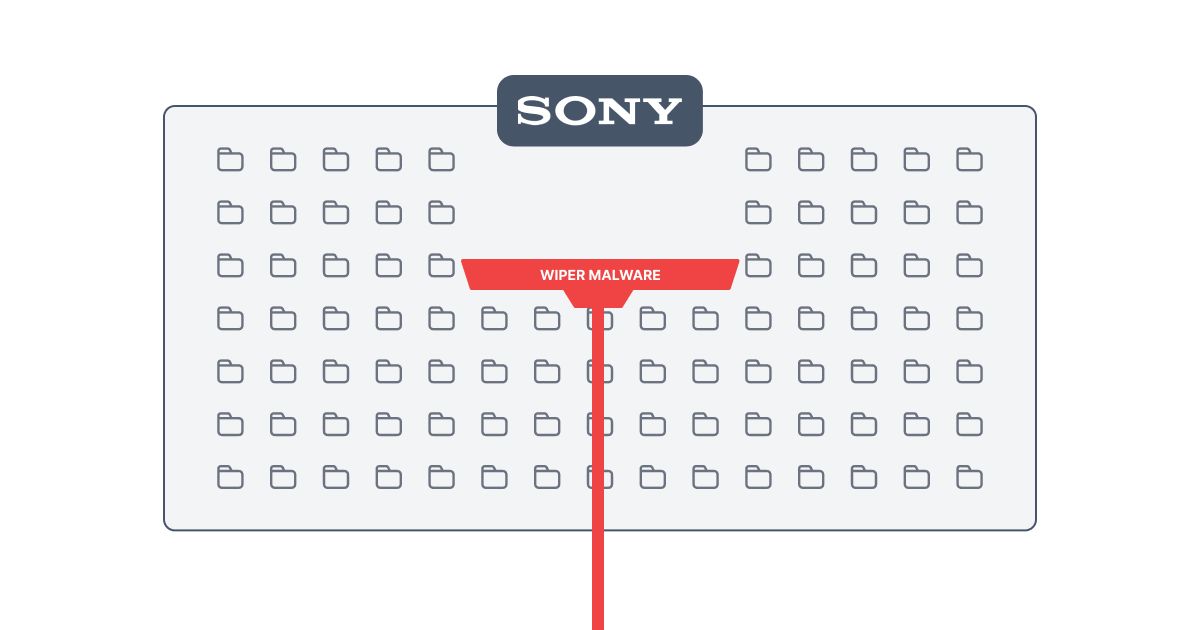
While the Sony breach might appear to be a series of well-executed steps, it's critical to remember that it likely involved a great deal of patience, skill, and an understanding of both human psychology and complex technical systems. The attackers had to stay under the radar while moving laterally across the network, avoid or disarm security measures, and finally execute a large-scale data exfiltration without triggering alarms. As the saying goes, "The devil is in the details," and in the case of the Sony breach, those details involved a perfect storm of technological exploitation and human deception.
Though the attackers were very meticulous with the execution of the attack, Sony's basic information security practices weren't that great either. Sony used to store sensitive information such as contracts, business transactions, business records, and other documents over email for long-term storage. Hence, their email-retention policy stored emails as old as 7 years on their servers. These servers also had files such as Admin usernames and passwords lying in insecure spreadsheets and Word files, showcasing inadequate credential management, which eventually helped the hackers in their attack.
Although the "Guardians of Peace" claimed responsibility, the actual identities of the hackers were initially unclear. The FBI, after a detailed investigation, publicly attributed the attack to the government of North Korea, asserting that the hack was in retaliation for an upcoming Sony film "The Interview," a comedy about a plot to assassinate North Korea's leader, Kim Jong-un. North Korea denied involvement but praised the hack as a "righteous deed.”
The Aftermath: Understanding the financial implications
In the aftermath of the cyberattack, Sony Pictures was left grappling with severe financial and reputational damage. The company incurred millions in immediate costs, including investigating the breach, restoring its network, and dealing with the fallout of leaked data. In response to threats of terrorism at theaters showing "The Interview," many major theater chains opted not to screen the film, and Sony canceled the theatrical release. However, they later decided to release it online and in select independent theaters.
In its financial report for the fiscal year ending March 2015, Sony Corporation estimated that the breach's direct costs, including incident response and network restoration, would total $15 million. However, this figure doesn't account for potential long-term costs such as legal expenses, regulatory fines, and the impact on Sony's reputation.
Moreover, the breach had severe operational impacts. With the IT network paralyzed, employees had to revert to using pen and paper. Unreleased movies were leaked online, potentially affecting box office sales. Confidential emails led to awkward revelations and strained relationships with talent and partners.
Takeaway: How could this have been prevented?
The Sony Pictures breach underlines a grim reality - a cyberattack can be more than just a data breach; it can disrupt business operations and cause severe reputational harm.
Infrastructure access management is crucial. 61% of all breaches involves credentials, whether stolen via social engineering or hacked using brute force. As we've seen, a single compromised credential can lead to a full-scale data breach. Organizations must implement solutions that ensure secure access to systems and networks. This means moving beyond traditional username-password combinations and embracing advanced solutions like Multi-Factor Authentication and Zero-trust Network Access.
The Sony Pictures breach serves as a stark reminder that in the digital world, everyone is a potential target. However, by leveraging modern tools and approaches, organizations can significantly enhance their security posture and keep their name out of 'Bits and Breaches.'
 SOC2 Type II
SOC2 Type II

